Workpackages
Project Structure
CONFIDENTIAL6G is structured around 6 WPs and has a duration of 36 months. The PERT chart provides an overview of the main interactions and dependencies between the WPs.
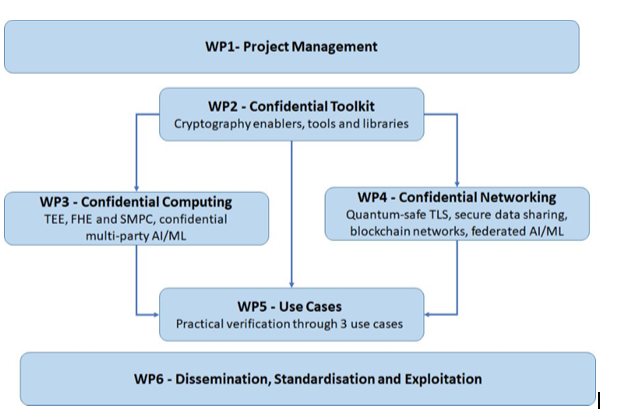
CONFIDENTIAL6G WP interactions diagram (PERT chart)
Work Package 1 – Project Management
Leader: WINGS ICT SOLUTIONS INFORMATION & COMMUNICATION TECHNOLOGIES IKE
WP1 is responsible for coordinating and managing the project and ensuring efficient, smooth and timely execution of all project activities. This will include maintaining and/or revising the project work plan when appropriate, ensuring the accurate and timely communication flow among project partners and the European Commission (EC) and realizing the project objectives within the agreed time frame and budget, at a high quality.
Work Package 4 – Confidential Networking
Leader: ALCATEL-LUCENT INTERNATIONAL SA
WP4 designs secure, future-proof and quantum-safe networking primitives, architecture and mechanisms needed to assure secure data exchange and sharing over the cloud-edge continuum. Furthermore, it develops the orchestration mechanism to improve data privacy by improving federated AI/ML in the context of confidential computing. Additionally, WP4 develops data verification and access control mechanisms leveraging on the modern blockchain network, which it further improves for privacy-preservation using cryptographic enablers developed in WP2.
Work Package 2 – Confidential Toolkit
Leader: NOKIA SOLUTIONS AND NETWORKS GMBH & CO KG
WP2 designs a toolkit for privacy preserving technologies and post-quantum cryptography. It defines cryptographic enablers for 6G privacy-preserving and confidential computation and networking. The toolkit involves a detailed analysis of the feasibility, practicality and hardware/software requirements in the implementation of those primitives. To showcase the usefulness of the toolkit, WP2 will apply the findings in one of the main 6G innovation drivers, namely the Enterprise/Utilities sector and specifically in ICS applications.
Work Package 5 – CONFIDENTIAL6G Use cases
Leader: TELEFONICA INVESTIGACION Y DESARROLLO SA
WP5 leverages the outcomes of WP2-WP4 and puts into practice the respective solutions in a cloud and edge computing testbed including both private and public cloud resources.
Work Package 3 – Confidential Computing
Leader: TEKNOLOGIAN TUTKIMUSKESKUS VTT OY
WP3 implements methodologies and mechanisms for confidential computing. Today, confidential computing is dependent on hardware extensions, so called Trusted Execution Environments (TEEs), and WP3 implements software abstractions and enablers needed to use these TEEs in a vendor-neutral manner. Additionally, modern cryptographic approaches will be developed, including Fully Homomorphic Encryption and Secure Multi-party Computation, and optimized for potential in practical use. Emphasis will be put on scenarios of collaborative AI applications, as well as on IoT edge.
Work Package 6 –Dissemination, Standardisation, and Exploitation
Leader: ZENTRIX LAB LLC
WP6 performs standardization, dissemination and exploitation activities and it represents a crucial element in order to ensure the impact of the project by closely engaging, from its beginning, with a diverse set of stakeholders and existing ecosystems and by implementing an effective bootstrapping and expansion strategy, relying on dissemination, exploitation and standardization.
